It is same the previous challenge so it is not necessary to write new writeup 🙂
Actually Challenge is not different than previous challenge.
Firstly, I examine the main function.

I find a string value that I predict license key.

I type a license key but it is not working and I back to source code. I realize the comment.

I change the letter in 0 and 2 indexes

Finally it is working.
I analysis the binary with ghidra.

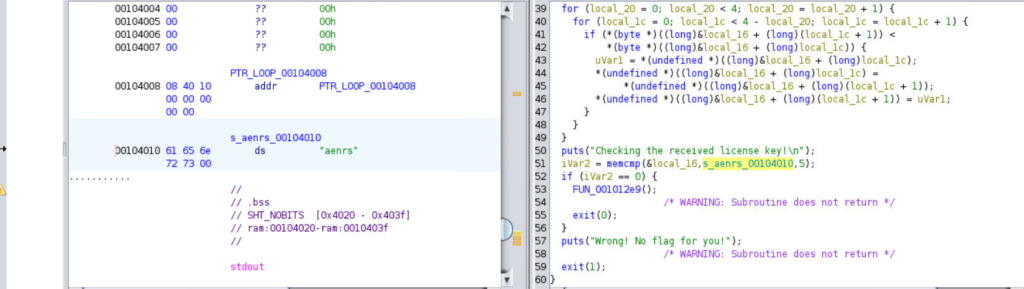
When I see the symboll tree I find a local_variable. Actually my purpose is that I see the main function and find a main function.

I find function that run the library and change the name as main. Sorry for the screen shot I ss after change its name.

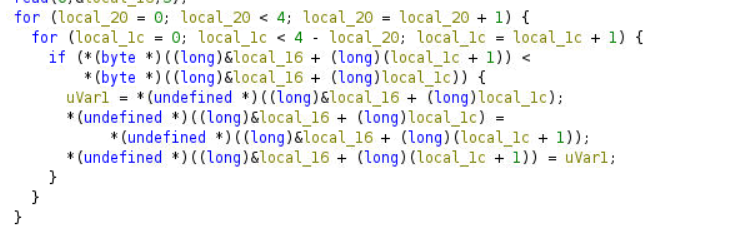
When I see main function. The most attention thing is that usage memcmp.

memcmp compares two memories according to the value you give. For more information
https://www.tutorialspoint.com/c_standard_library/c_function_memcmp.htm

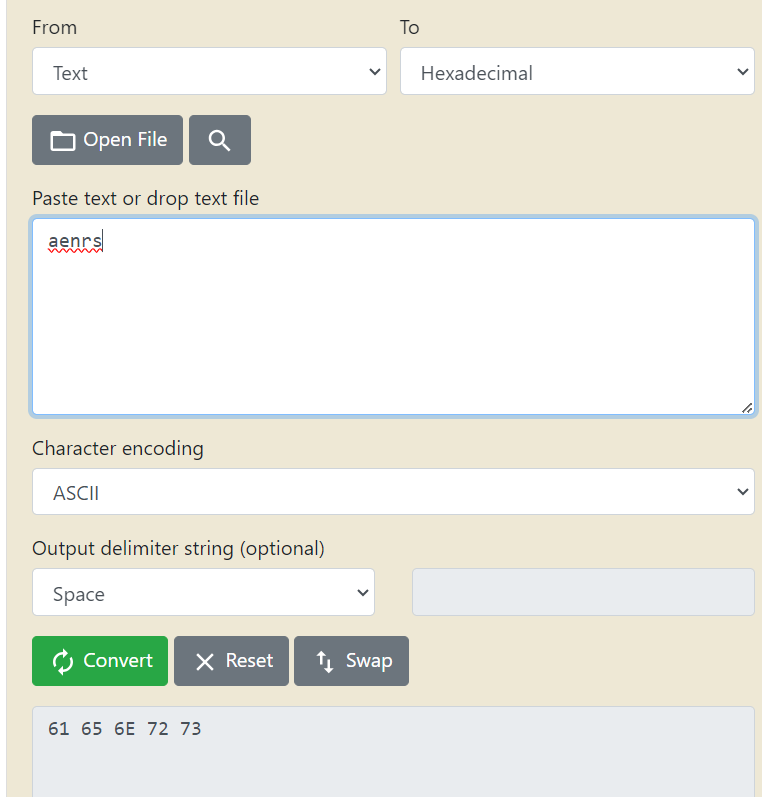
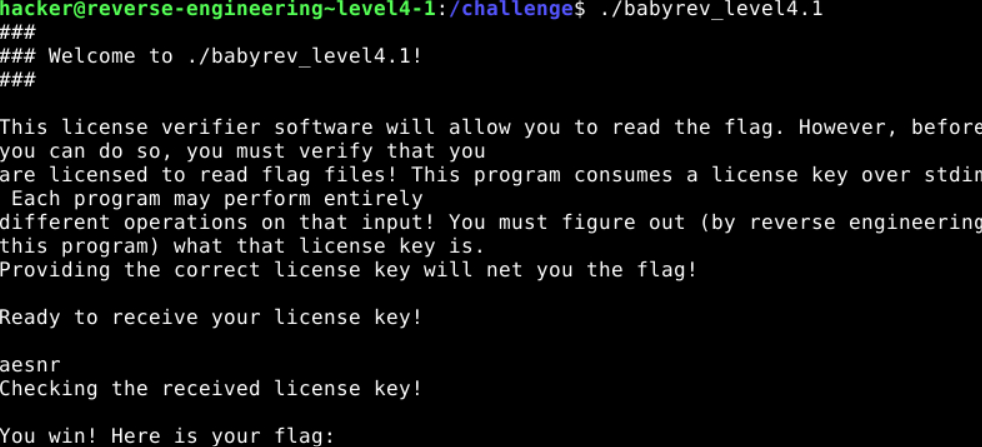
I see the memory “eqbdc” and when I type the keyword. It is working. 😀


I start the new challenge that is related reverse engineering. Moreover I continue to add many writeup about other topics.
Let’s start to talk about first challenge.
I try to solve challenges that I mention the first paragraph. I try to talk about first challenge.
I start the machine and run the binary.

It specifies that expect result 75 6d 6e 75 64
So I convert the value to ASCII.

And I type the ASCII value after I run the binary. It runs successfully

